It is possible to use AAD as an authentication source for users accessing the AWS console. Follow the steps described here, and you won’t need to maintain two authentication sources.
Creating the application on Azure
| # |
Action |
Screenshot |
| 1 |
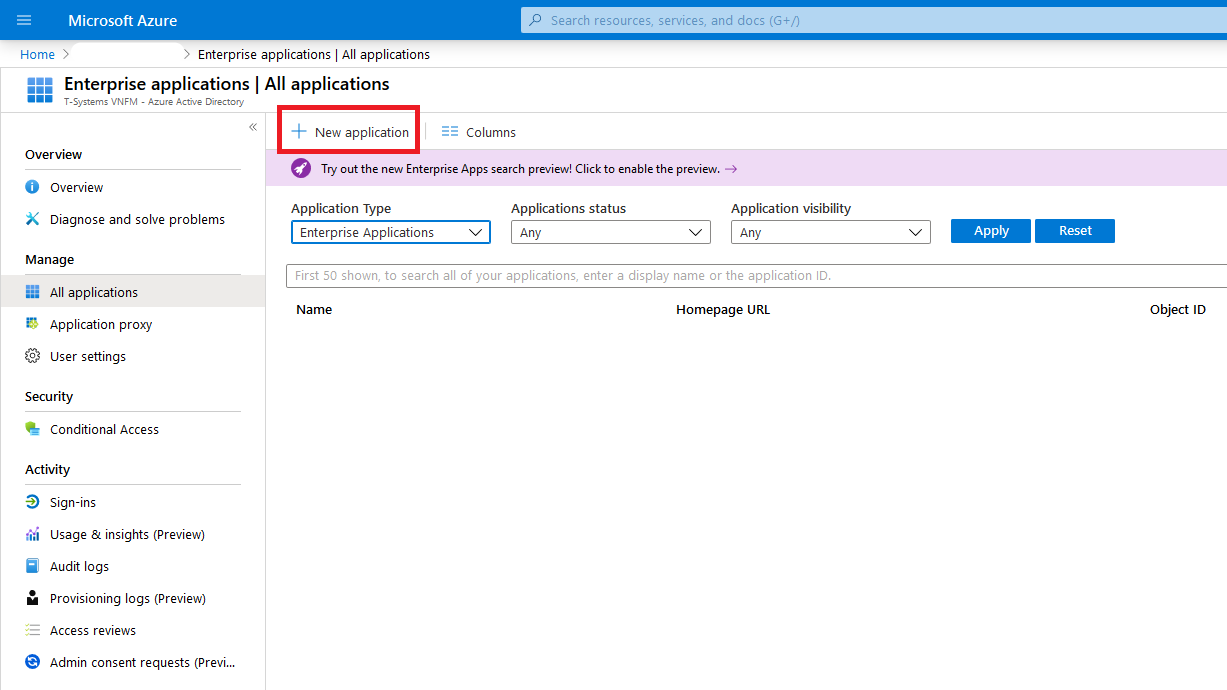
Create a new Enterprise Application under the AAD settings. |
|
| 2 |
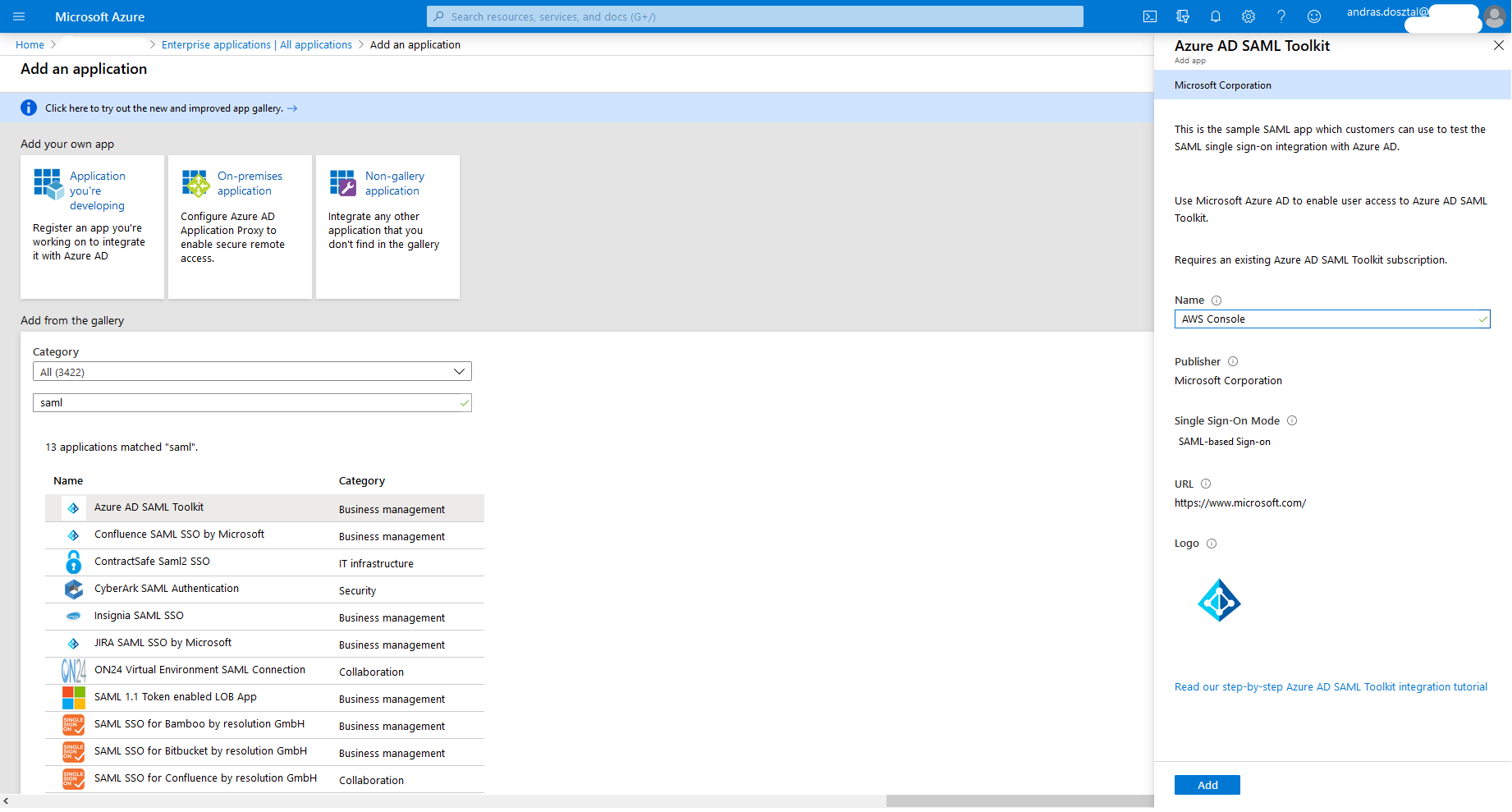
From the applications, select Azure AD SAML Toolkit, and give it a name (AWS Console in this case). |
|
| 3 |
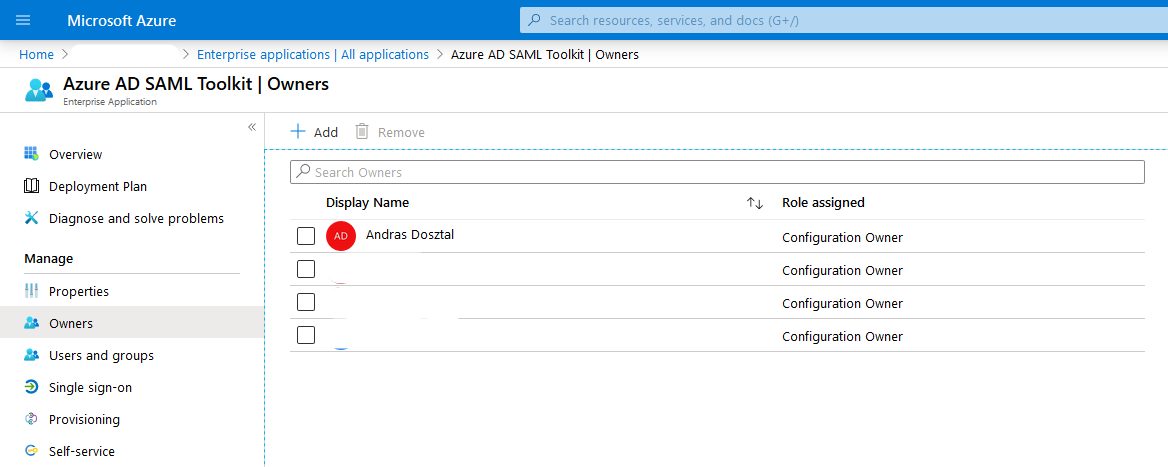
After the application is added, choose its Owners. |
|
| 4 |
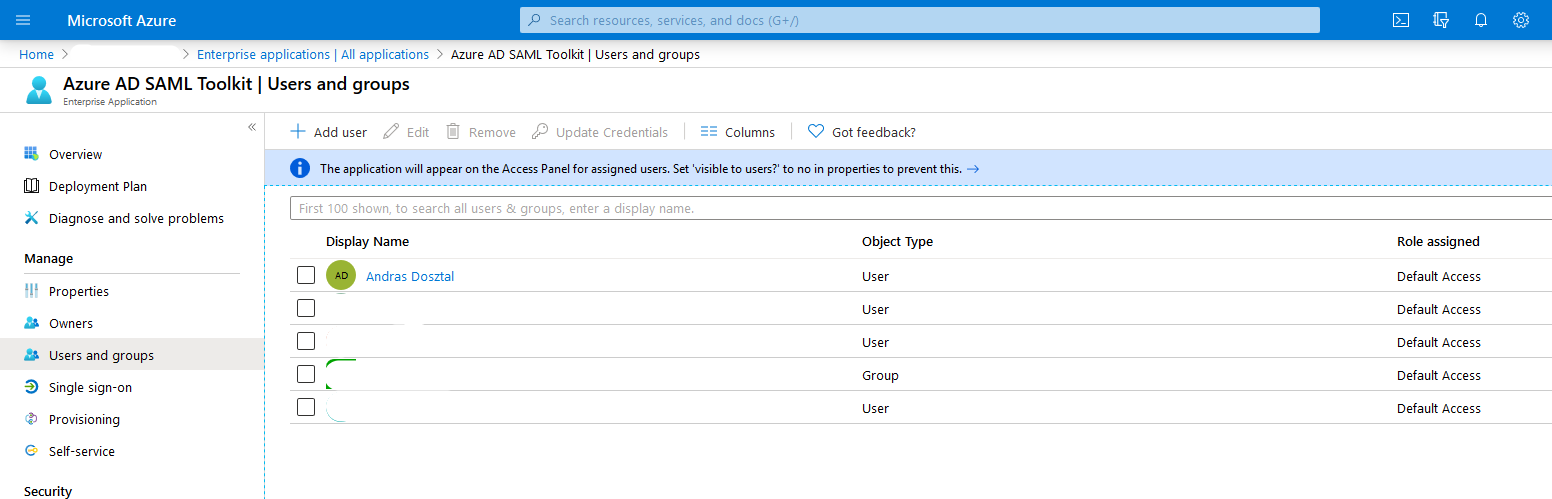
Add the Users and groups who can use this application. Note: Groups can only be added with Premium AAD subscriptions. |
|
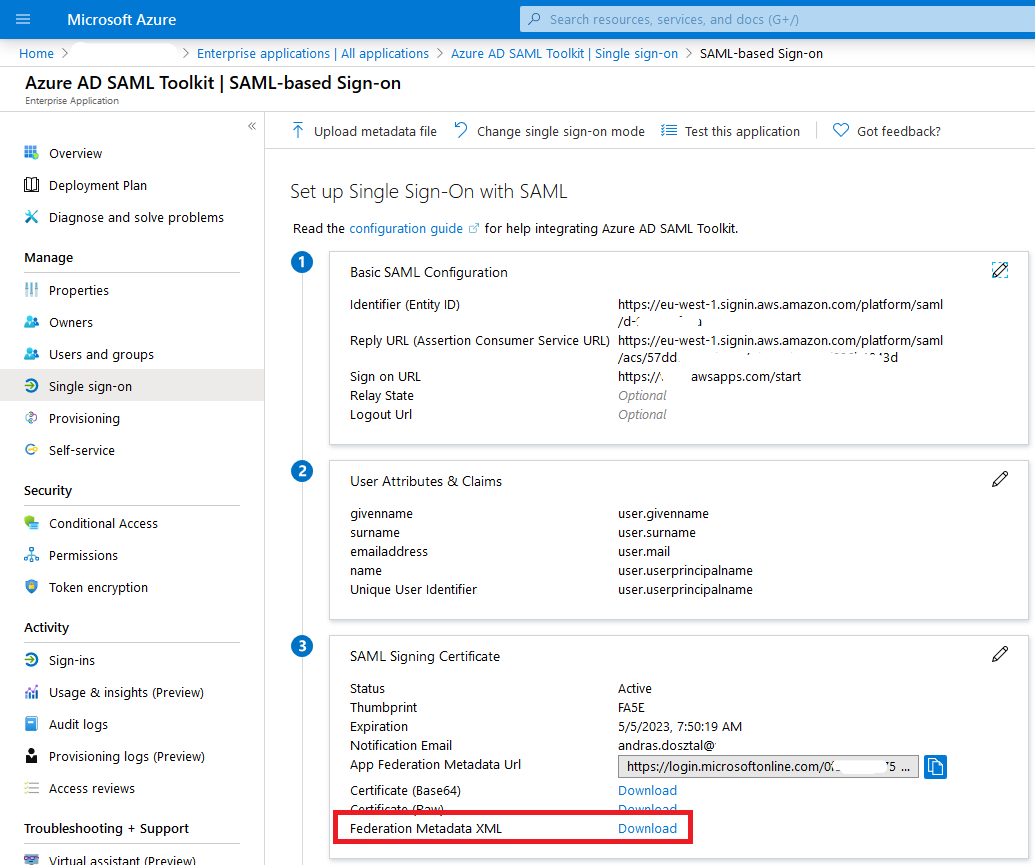
| 5 |
Go to Single sign-on and download the Federation Metadata XML. |
|
| |
|
|
Changing Identity provider on AWS
| # |
Action |
Screenshot |
| 6 |
If hasn’t done before, create an Organization and add your account to that. |
|
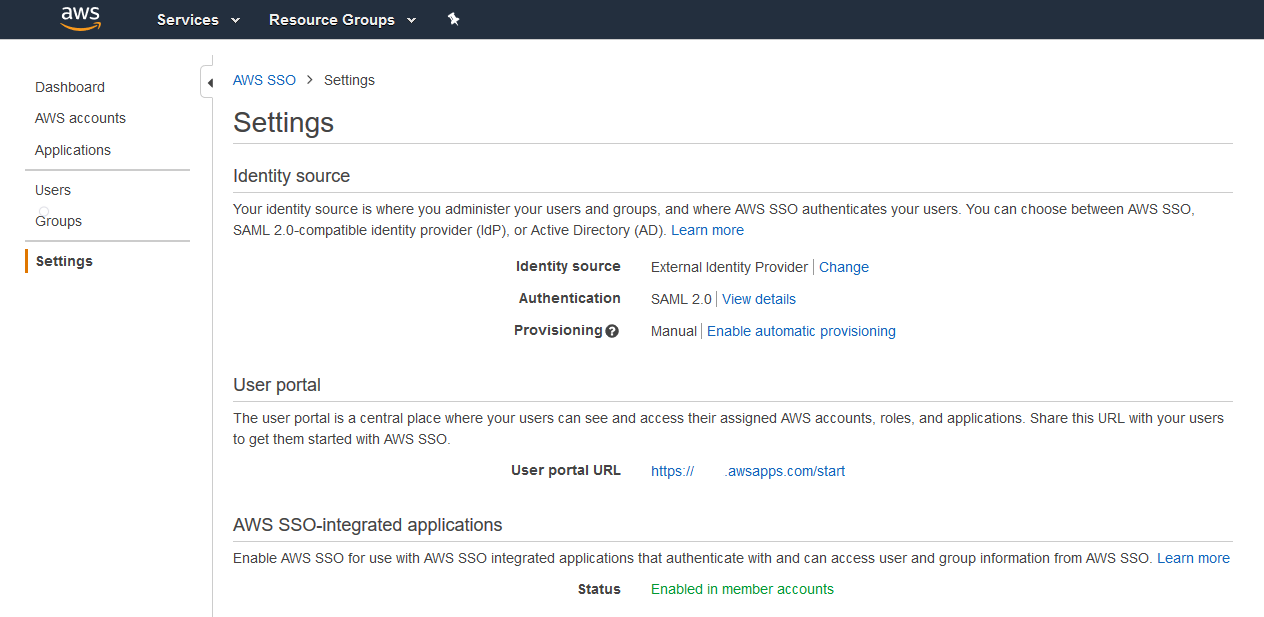
| 7 |
Go to AWS SSO and click on Choose your identity source. |
|
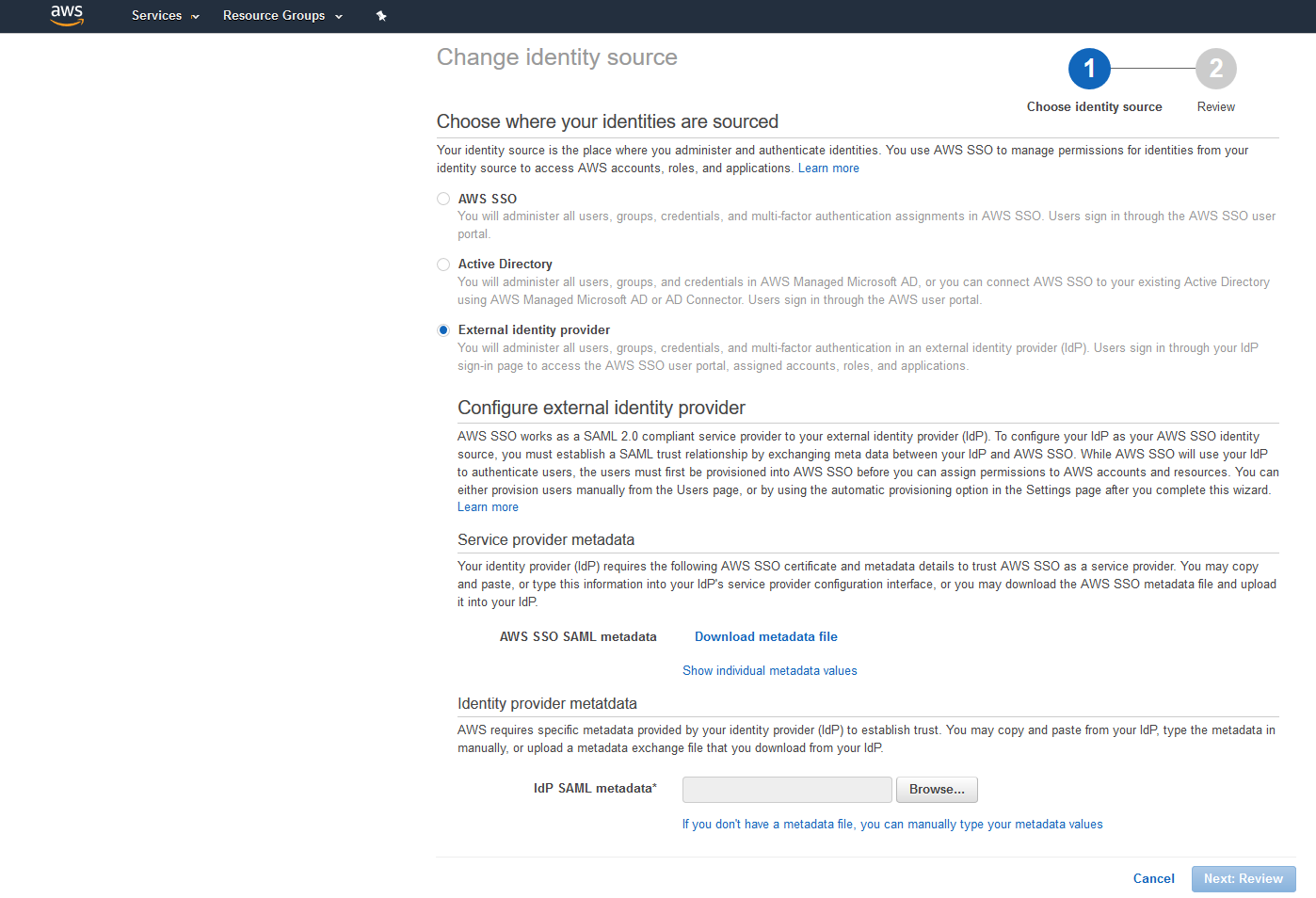
| 8 |
Select External identity provider, then upload the Metadata XML that was downloaded previously from Azure. |
|
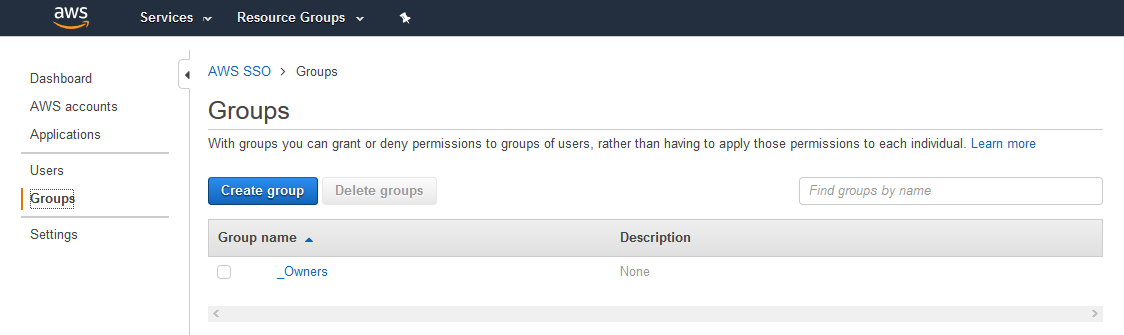
| 9 |
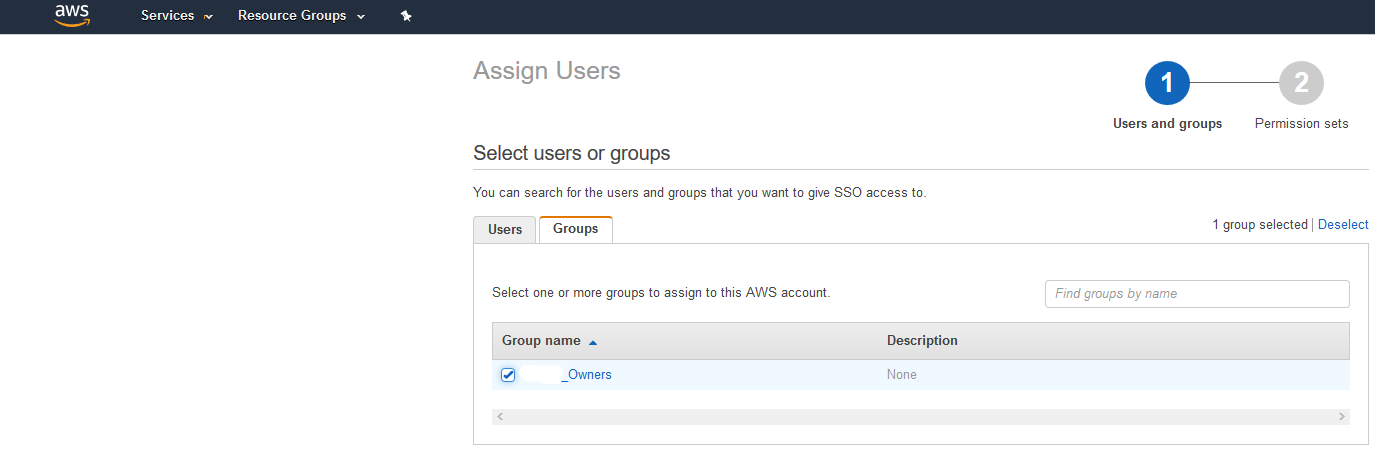
Create a Group for the Azure users. |
|
| 10 |
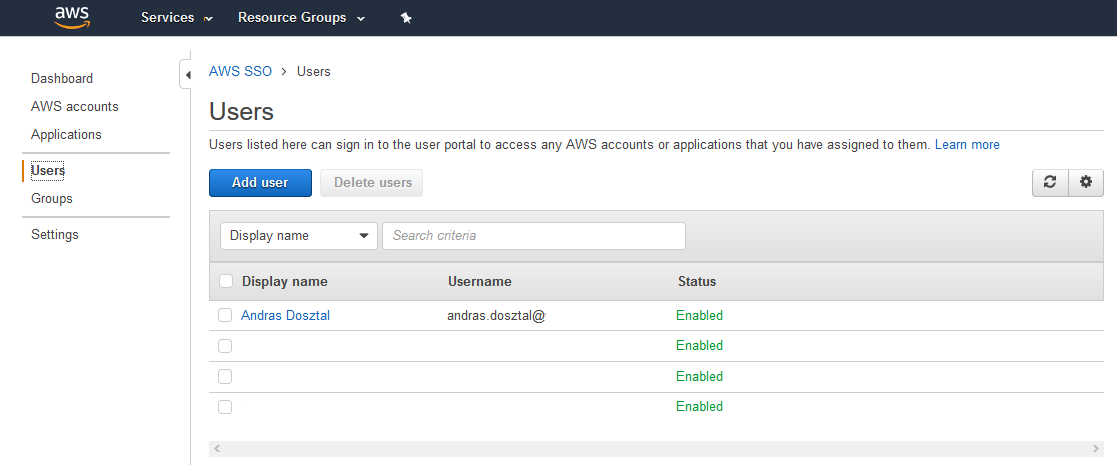
Create the Users who were in AAD, assign them to the group created in the previous step. |
|
| 11 |
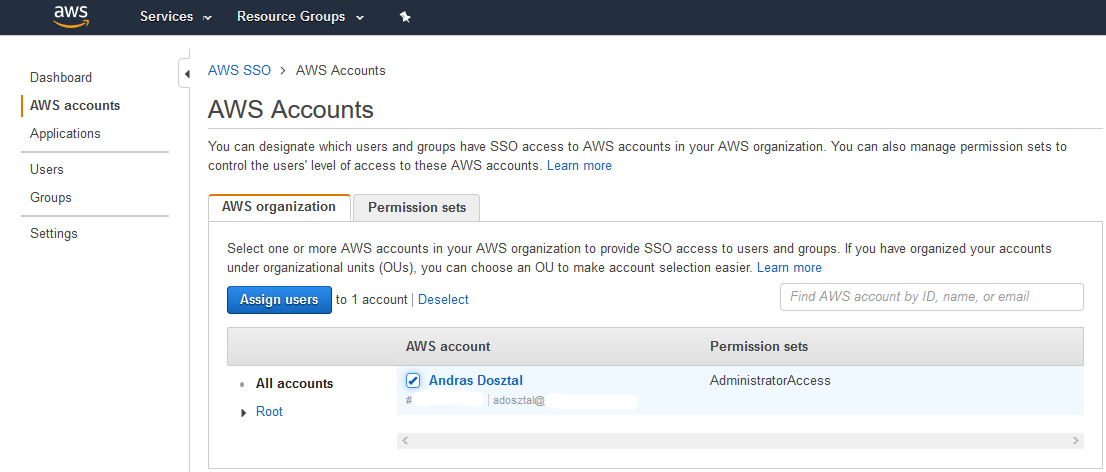
Go to AWS accounts, and create a Permission set for the to be associated users. |
|
| 12 |
Link the users to the AWS account. |
|
| 13 |
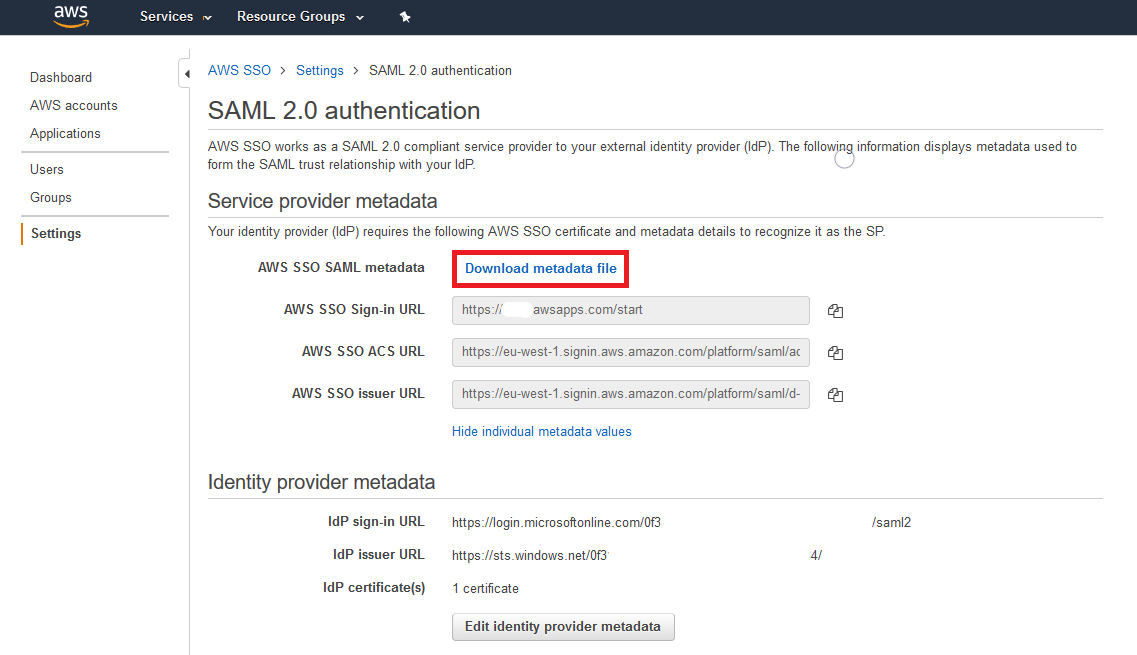
Go to Settings, click on View details next to “Authentication / SAML 2.0”, then click on Download metadata file. |
|
| |
|
|
Finalizing SAML configuration on Azure
| # |
Action |
Screenshot |
| 14 |
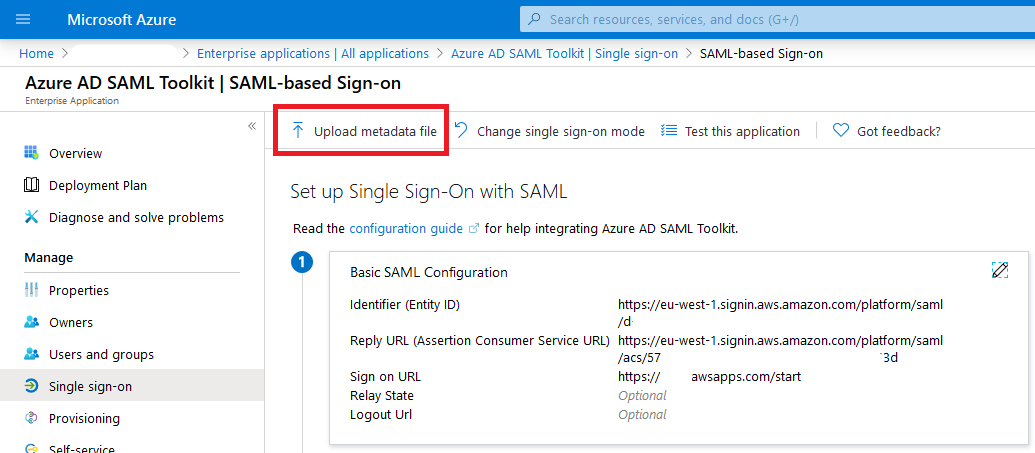
Go back to the Enterprise application on the Azure portal, and upload the metadata file that was downloaded in the previous step. |
|
| 15 |
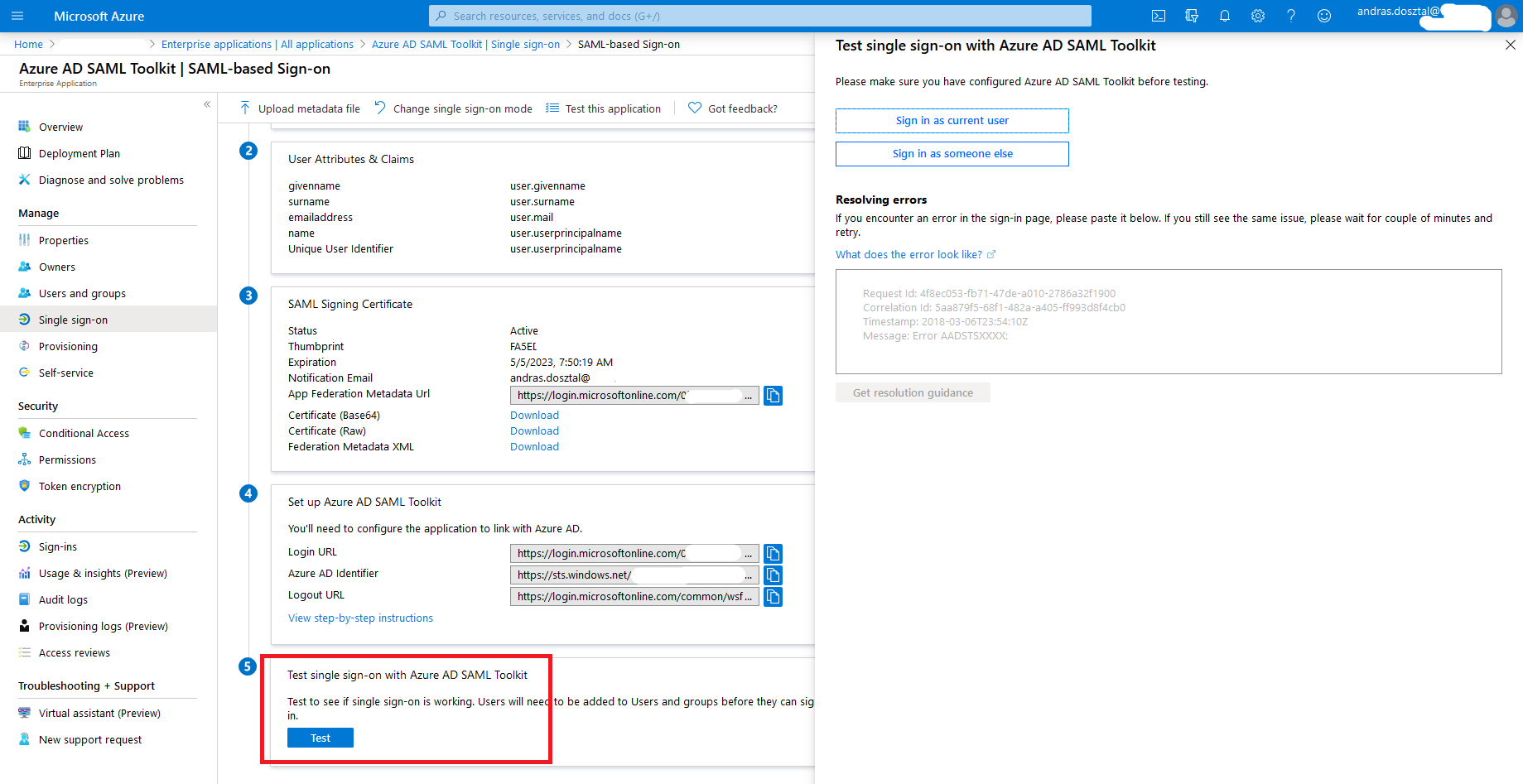
It is advised to the test the SSO on the Azure portal. |
|
| |
|
|
Limitation
Users are not synchronized from AAD but must be created on AWS. This can be done using automation scripts but these need to be developed.